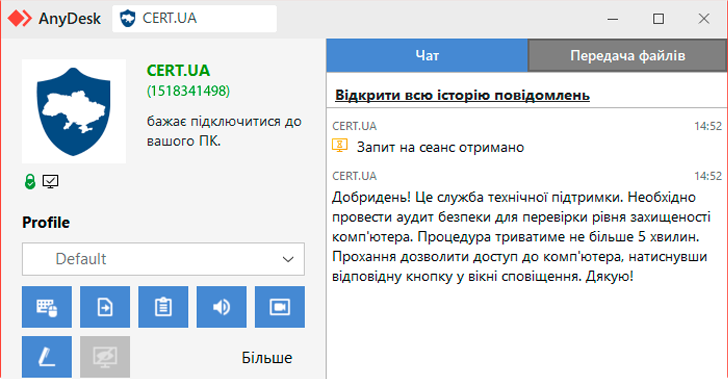
The Computer Emergency Response Team of Ukraine (CERT-UA) has issued an urgent warning about an ongoing cyberattack campaign where unknown threat actors are impersonating the agency to trick individuals into allowing remote access through AnyDesk, a remote desktop software. The attackers are sending deceptive connection requests, claiming that the purpose is to conduct an audit and assess the “level of security” of the target system.
CERT-UA has clarified that while the agency may, in certain situations, use remote access software such as AnyDesk for legitimate purposes, these actions are always carried out through prior agreements with the owners of the targeted systems, and only after communication through officially approved channels. The warning comes as part of a larger cybersecurity effort to prevent the exploitation of user trust and to inform organizations about the tactics being used by these threat actors.
For these attacks to succeed, the remote access software must be already installed and operational on the victim’s device. Moreover, the attackers would need to have access to the target’s AnyDesk identifier, which could be obtained through various means. This suggests that the attackers might be collecting identifiers through earlier compromises or social engineering tactics.
To protect against such attacks, CERT-UA advises organizations to enable remote access software only when necessary and for the shortest time possible. Additionally, any remote access requests should be coordinated strictly through official channels to minimize the risk of falling victim to these social engineering attempts.
The announcement comes amid broader concerns about the growing cyber threat landscape in Ukraine. The State Service for Special Communications and Information Protection (SSSCIP) recently revealed that the agency’s incident response center detected over 1,000 incidents in 2024. The majority of these events, approximately 75%, involved malicious code and intrusion attempts, underscoring the persistent nature of cyber threats facing Ukraine.
Several cyber threat clusters have been identified as the primary actors behind these attacks. Among them, UAC-0010, also known as Aqua Blizzard and Gamaredon, was responsible for 277 incidents, focusing on cyber espionage and information gathering. Other groups, such as UAC-0050 and UAC-0006, were linked to financial theft and information-psychological operations, with 99 and 174 incidents, respectively.
Another significant development is the discovery of 24 previously unreported .shop domains likely connected to the pro-Russian hacking group known as GhostWriter (TA445, UAC-0057). These domains were used in a variety of campaigns targeting Ukrainian entities, providing further evidence of the group’s ongoing activities. Security researchers found that these domains shared the same generic top-level domain (gTLD) and were hosted on Cloudflare’s name servers, with several having a robots.txt directory configured, which may indicate intentional evasion of security scans.
As the war between Russia and Ukraine enters its third year, cyberattacks have also targeted Russian organizations. Recently, F.A.C.C.T. cybersecurity attributed a spear-phishing campaign to the Sticky Werewolf actor, a pro-Ukrainian cyber espionage group. The campaign aimed at Russian research and production enterprises delivered a remote access trojan known as Ozone, which grants remote control over infected Windows systems.
Sticky Werewolf, according to F.A.C.C.T., predominantly targets state institutions and industrial enterprises in Russia. However, previous reports from Israeli cybersecurity firm Morphisec have raised doubts about the connection between the group and Ukraine, highlighting the complexity and uncertainty surrounding cyber attribution in the current geopolitical landscape.
Additionally, other threat actor groups targeting Russian entities in recent months include Core Werewolf, Venture Wolf, and Paper Werewolf (also known as GOFFEE). The latter has employed a malicious IIS module named Owowa to facilitate credential theft, further highlighting the sophistication of these cyber campaigns.
The increase in cyber activity and the rise in targeted attacks underscore the growing importance of robust cybersecurity measures, not just for Ukrainian entities but for global organizations operating in vulnerable environments. As the digital battlefield expands, both defensive and offensive cyber operations continue to shape the conflict, with ongoing campaigns aiming to disrupt operations, steal sensitive information, and influence outcomes.
For organizations in Ukraine and beyond, this serves as a reminder to stay vigilant against cyber threats. Remote access tools like AnyDesk can be invaluable for legitimate purposes, but they also present significant risks when misused by malicious actors. CERT-UA’s warning emphasizes the need for proper coordination and the use of secure channels when granting remote access to any system.